Active Directory Data Model
Active Directory uses the LDAP data model, which is derived from the X.500 data model and, consequently, Active Directory implements many of X.500 features. However, Active Directory is not a full X.500 directory service.
Classes, Objects, and Attributes
The schema dictates which object classes and attributes a given forest supports. The base schema that ships with Windows Server 2003 supports 191 object classes (142 in AD2000) and 1070 attributes for those classes (863 in AD2000). Each attribute has one of 23 syntaxes, such as Integer 14, Unicode string "abc", or Generalized time 04/26/2000 2:59:01 PM.
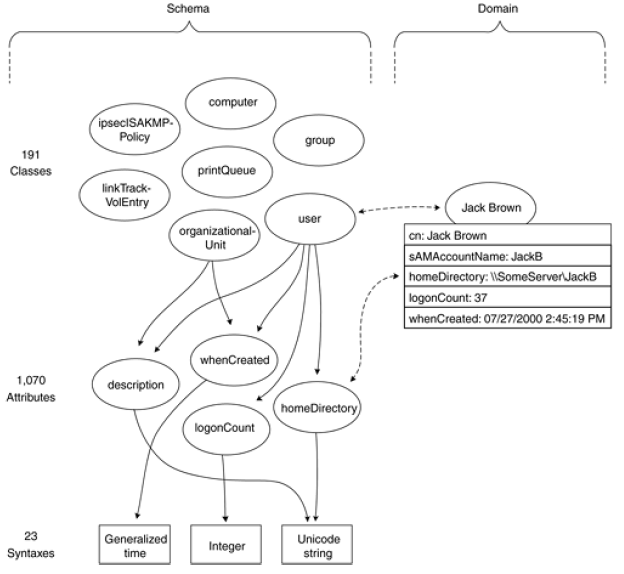
The user class uses 257 attributes of the pool of 1070. Active Directory implements most of the X.500 standard classes, but not quite all. The classes that it does not implement are alias and strongAuthenticationUser.
For example, the Jack Brown object is an instantiation of the user class. Just as the class contains a number of attributes, the instantiated object contains the values for those attributes. However, only some of the attributes for a class are mandatory, which means that they must contain a value (a single-valued attribute such as homePhone) or values (a multivalued attribute such as otherHomePhone). Most of the attributes for a given class are optional; that is, they may contain a value, but more often they don't.
Container and Leaf Objects
Active Directory objects of some classes are container objects, and the objects of the remaining classes are leaf objects. If you compare this to a file system, container objects correspond to folders and leaf objects correspond to files. We call these two types of classes container classes and leaf classes.
One obvious example of a container class is organizationalUnit. There are also many others, however, because a total of 67 classes of the base schema are container classes and 124 are leaf classes (56 and 86 in AD2000). Interestingly, user is also a container class; user objects may contain nTFRSSubscriptions and classStore objects.
Indexing and the Global Catalog
An Active Directory database can contain thousands or even millions of objects. Therefore, we obviously need indexing to locate the right object or objects fast. Of the base schema, 69 attributes are indexed (64 in AD 2000), examples being givenName, sn (Surname) and birthLocation. Searching and retrieving objects via indexed attributes is naturally much faster and efficient than using nonindexed attributes.
The global catalog helps in making local searches in a multidomain forest. 151 attributes of the base schema are part of the global catalog (138 in AD2000), including cn, userPrincipalName, givenName, sn (Surname), and printStaplingSupported.
Partitions
An Active Directory domain is a unit of replication, A unit of replication is called a partition, or sometime a naming context (NC). This means that a domain is a partition. However, domain is not the only of partiition. Every domain controller holds a copy of the following three partitions:
- The domain partition, where users, groups, OUs, and such reside.
- The schema partition, where schema classes and attributes reside.
- The configuration partition, where information on the forest structure resides, such as the sites and domains.
Information in the first partition (i.e., users, groups, and so on) is replicated among the domain controllers of one domain, whereas the schema and configuration partitions are replicated among all domain controllers in the forest. A copy of a partition in a given domain controller is called a replica.
The domain controller that are designated as global catalog servers hold a partial copy of all other domain partitions of the forest. A partial copy contains all objects, but it contains only those attributes that are part of the global catalog.
The following figure shows the partitions of one sample forest. The two right most partitions exist in every domain controller, whereas the sales.sano.com and sano.com partitions exist only in the domain controllers of the correspondling domain.
